How to use Windows as an Evolve Virtual Appliance
Evolve provides the ability to generate pre-configured Evolve Virtual Appliances for a variety of platforms, such as VMware, Hyper-V, AWS, Azure and Docker – as detailed within our Getting Started with the Evolve Virtual Appliance blog post.
In addition to these platforms, a Windows host can always be utilised as an Evolve Virtual Appliance, as detailed in the steps below.
Step 1: Download the VPN Gateway configuration from the Evolve Console. Navigate to Security Zones > Gateways and click the Download button for the relevant VPN Gateway:
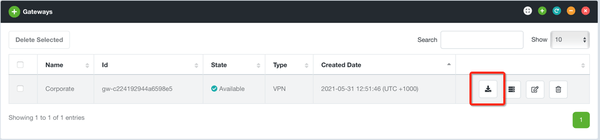
Step 2: Evolve will provide a ZIP file with the required configuration files, including your corresponding Evolve Certificate for trusted encryption and authentication.
Step 3: Download an OpenVPN client from the following source:
Step 4: Unzip VPN gateway configuration into the:
- C:\Program Files\OpenVPN\config
Step 5: Rename evolve.conf to evolve.ovpn
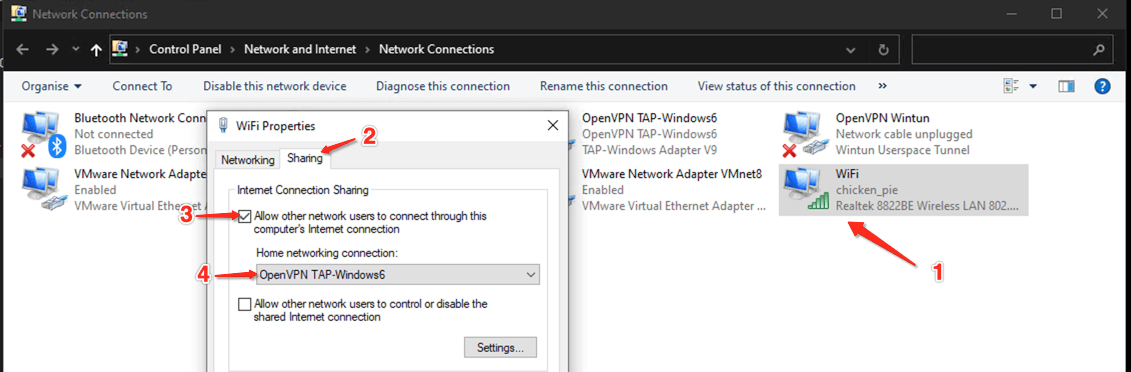
Step 6: Navigate to the Control Panel > Network and Sharing Centre > Change Adapter Settings. Enable Internet Connection sharing on your LAN interface, typically named Ethernet, selecting the OpenVPN TAP interface to share with:
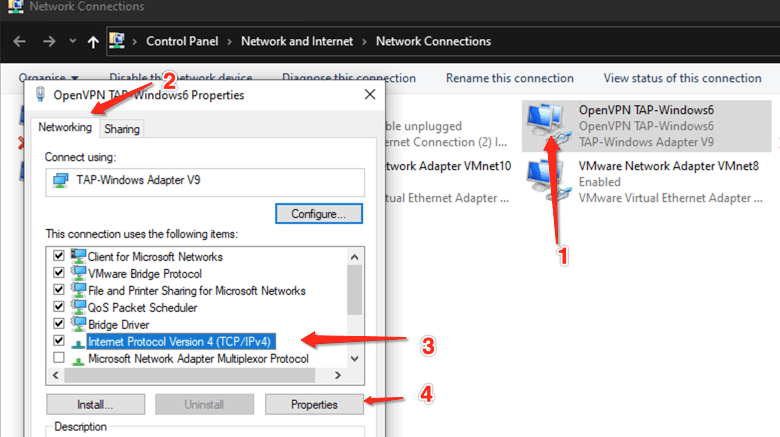
Step 7: Change OpenVPN TAP interface back to DHCP addressing*:
- Step 7.1:
- Step 7.2:
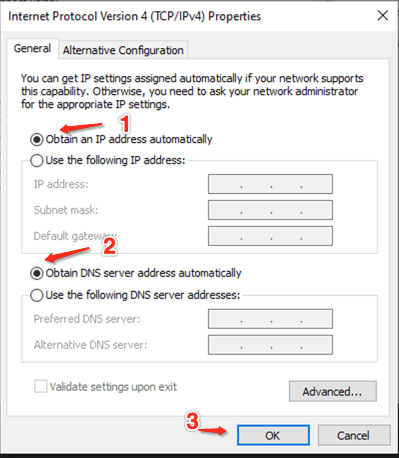
*The sharing will set a static IP, which we don’t want.
Step 8: Connect VPN, there will be an OpenVPN GUI as an option:
Step 9 – Done!
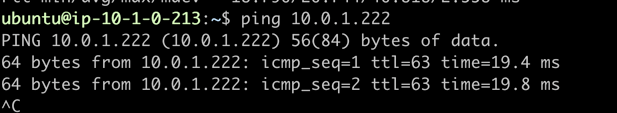
You’ll see traffic going across VPN to host on the network:
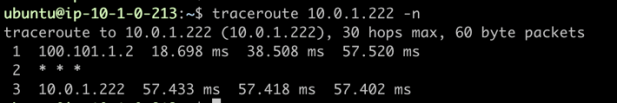
And traceroute too:
Now that we’ve shared how to use Windows as an Evolve Virtual Appliance, book a demo with our Cybersecurity Experts and see how Evolve can augment your security team with specialist security automation and orchestration capabilities.



