Product > EvolveSC Automated Supply Chain Monitoring

Detect critical Supply Chain Risks from your third-party vendors and avoid the #1 way that companies get breached

Identify attacks that may be used to compromise
your third-party suppliers and your business
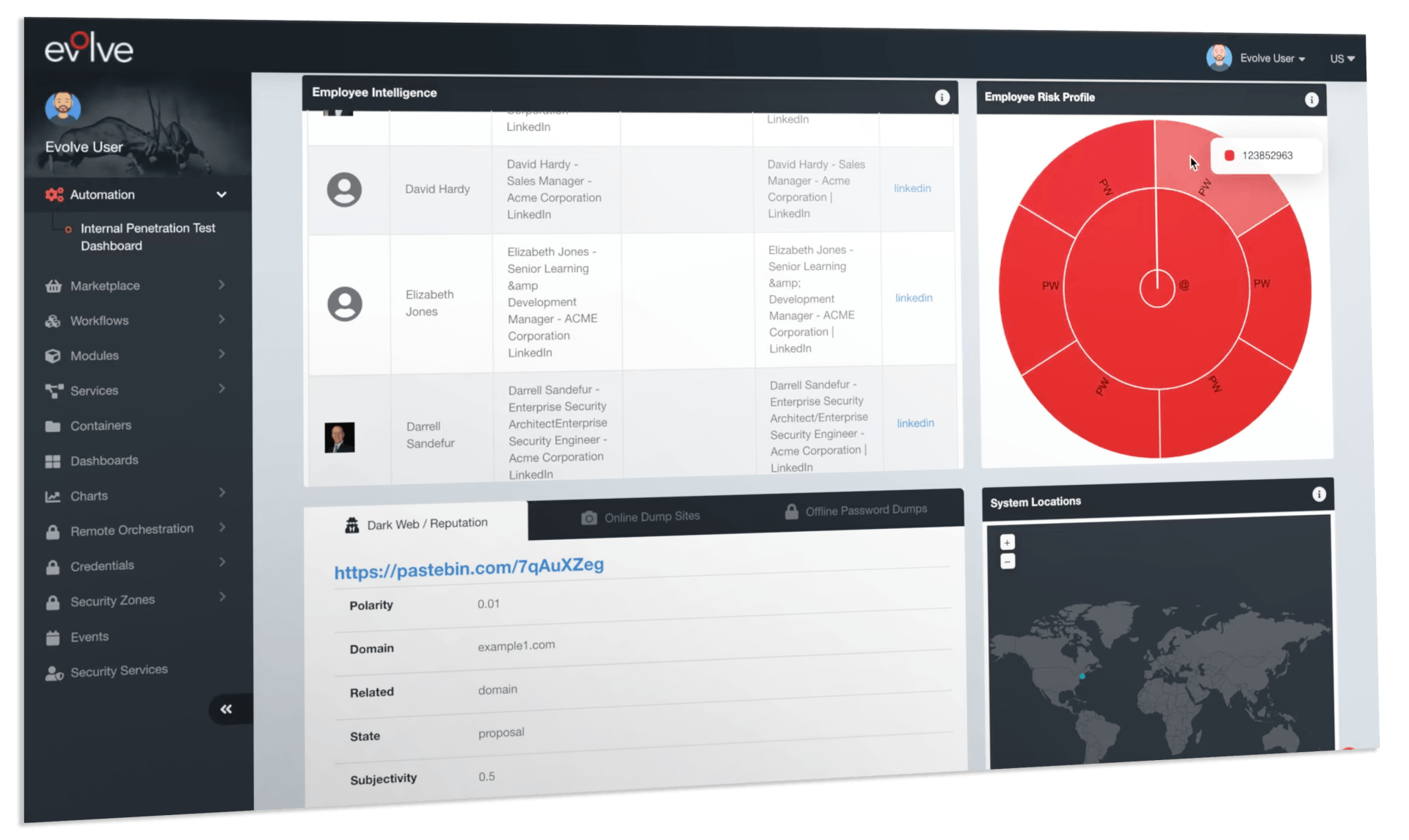
Critical Supply Chain Risks
The #1 way companies become breached is through leaked passwords from third-party security breaches or by abusing the inherent trust relationship with third party software or service providers to attack your business. This means that managing the security of your supply chain is more critical now than ever. Improve your Supply Chain Risk Management Monitoring!
How it Works
Security teams can gain regular insights into their supply chain risks without the overheads of gaining approvals. EvolveSC helps organizations minimize the time to detect critical risks across all their third-party vendors – completely passively.
Proactive Supply Chain Security
Automatically collect and generate intelligence about your Supply Chain to identify attacks that may be used to compromise your third-party suppliers, and subsequently your business.
Key Features
✓
Employees most susceptible to threats
✓ Email address prediction and verification
✓ Leaked usernames and passwords
✓ Compromised systems and services
✓ Suspicious dark web communications
✓ IP and DNS reconnaissance
✓ Unknown domains and system
✓ Real-time exploit locator
✓ Automated exploit configuration

