Product > EvolvePT Automated Penetration Testing

Get cost-effective security validation by regularly testing your IT infrastructure
Execute on-demand Automated Penetration Testing to identify key attack vectors and security flaws faster than even before
Orchestrate scalable Automated Penetration Testing environments specifically for the type of penetration test that you need
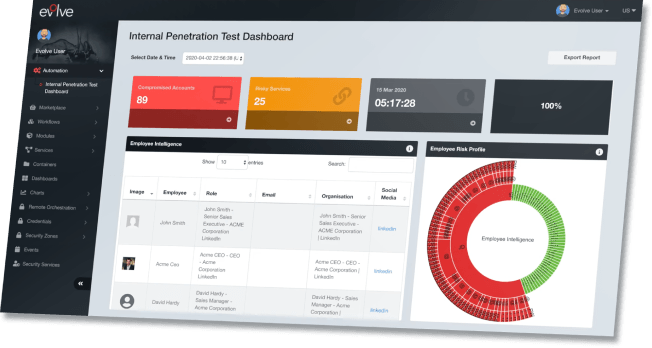
Automated Internal & External Infrastructure Penetration Testing
Effectively reduce risk through automated integration of your reconnaissance results, system and software fingerprinting, real-time exploit and malware searches, automated attacks and exploitation.
Greater Coverage
With Evolve’s location-agnostic penetration testing capabilities you can allow multiple attack vectors to be tested in the cloud and across your organization’s security zones. This provides far greater depth and coverage compared to vulnerability scanning, including organization reconnaissance, man-in-the-middle attacks, automated exploitation, privilege escalation, and lateral movement.
On-Demand
Evolve lets organizations execute on-demand automated penetration testing to identify key attack vectors and security flaws faster than ever before. We also make sure new vulnerabilities and attacks are tested as they are released to enable faster risk identification and security compliance throughout the year.
Key Features
✓ Employee Social Media Reconnaissance
✓ Evolve Compromised Account Search
✓ Software Vulnerability Identification
✓ Multi-Engine Vulnerability Scanning
✓ Optimized Exploit Configuration
✓ Credential Memory Extraction
✓ Leaked Passwords Lateral Movement
✓ Report Quality Assurance
✓ Risk Prioritization

With Evolve Automated Penetration Testing you get a lot more coverage:
| EvolvePt | Vulnerability scanning | |
|---|---|---|
| Phase 1: Internet Reconnaissance | 100% | 17% |
| Phase 2: Fingerprint and Scanning | 100% | 0% |
| Phase 3: Attack and Exploitation | 100% | 60% |
| Phase 4: Post-Exploitation and Lateral Movement | 75% | 8% |
| Phase 5: Reporting | 87% | 0% |
| Covarage Score | 100% | 59% |