Penetration Testing Services
Our Penetration Testing Services combined with security automation proactively identify the most exploitable security vulnerabilities of your infrastructure before a malicious actor does
+20
Years of Penetration
Testing Experience
+1000
Customers Tested
& Protected
+10
Years teaching
at BlackHat
Threat Intelligence’s
Penetration Testing Services
Our Principal Security Consultants Team helps you mitigate security risks and prevent future data breaches and losses.
A Certfied Pentester team to meet your needs
Our team of highly experienced Principal Security Consultants work closely with you to protect business critical data and applications from both damaging external and an emerging trend of equally as significant internal threats.
The Consultants that will run your projects teaches advanced penetration testing training at Black Hat USA, Black Hat Europe and are part of the Review Board for Black Hat Asia.

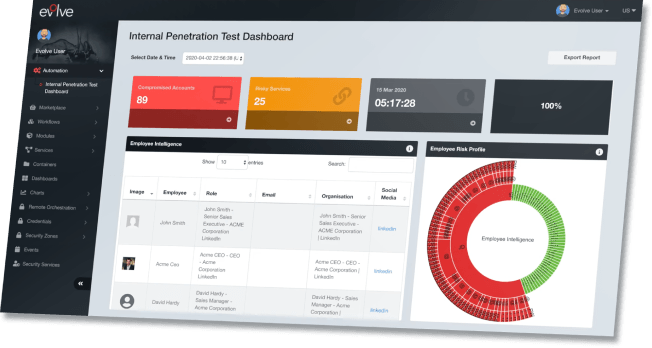
Our team will tell you what to fix and how to get it fixed
Combining our certified specialist security team, with up to 20 years experience each, and our Evolve Automated Penetration Testing capabilities, we streamline the engagements by automating time-intensive activities to deliver greater coverage and increase the quality of your outcomes.
“Threat Intelligence consistently find more vulnerabilities that allow us to proactively prevent security breaches. So much experience and knowledge in one team”
CISO
Health Industry
Enterprise
As one of the top pentesting companies in Australia, Threat Intelligence offers a diversity
of penetration testing services
Web Application
Internal Infrastructure
API and Web Service
Thick Client Applications
PCI (Peripheral Component Interconnect)
Endpoint Device Exploitation
IOT (Internet of Things)
Wireless
Mobile App and API
Copyright Protection Bypass
Phishing and Social Engineering
Read Team
Security and Network Device
OT and SCADA
External Infrastructure
Cloud and Virtualization


